Resilience and security

The dangers of digital disruptions
While the new digital reality has created enormous opportunities, it has also brought new threats and risks, and it is vital that systems, networks and services are resilient and secure. Despite an increasing number of high-profile incidents, many companies have still not woken up to the risks that technology can pose. “If you think the Fourth Industrial Revolution is something you can avoid, then history is against you,” says Ian Buffey, a Cyber Leader at Atkins. “It’s going to happen. The question is: how do we allow it to happen in a way that is safe?”
Devices, systems and networks are becoming more interconnected, even though many were not designed for that degree of interconnectivity. New computer-based “cyber physical” systems that operate physical infrastructure and/or machinery can make assets more vulnerable. “The new digital reality is a highly connected world, and with that comes multiple attack threats,” says Mark Fielding-Smith, Digital Rail Director at Atkins. He continues, “Across critical national infrastructure such as railways and air traffic control, we are enabling the change from analogue, decentralised control systems to more digital approaches, with safety-critical systems increasingly connected to non-critical systems.”
As systems become more complex, it becomes more difficult to assure that all safety and security aspects have been addressed, and to demonstrate that a system or service is safe and secure from outside attack, adds Ian Glazebrook, one of Atkins’ specialists in Safety Critical Software Systems.
-
The IT and digitalisation isn’t the point of managing the transition between old and new technology, the point is to make things more efficient, easier and to allow customers and people to focus on the real issues rather than focusing on processes and systems.
 Anonymous
Anonymous
And while an attack on a physical asset is often visible, for example from a denial of service perspective, software attacks are much harder to detect and mitigate. “Often you don’t know of an intrusion until the system fails, and even then, the system tends not to show what has caused the software failure,” says Glazebrook.
But failure creates clear safety, environmental and business risks, with consequential impacts on companies’ reputations, and ultimately their bottom lines. As the dangers of digital disruptions grow and become clearer, regulators and lawmakers have started to take note. Just as the European Union’s General Data Protection Regulation will punish companies that lose customers’ personal data when it comes into force in 2018, the EU’s Network and Information Systems Directive (NISD) addresses outages caused by delivery service failures in critical national infrastructure.
NISD is not the first legislation-backed attempt to address the risk to critical national infrastructure posed by cyber-attacks. The North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) regulations are backed by fines of up to $1 million per violation, per day. NERC-CIP applies to assets of specified criticality in the US and Canadian Bulk Electricity System. The NERC-CIP regulations have been through a number of iterations, and there are lessons to be learned from their growing pains. Unlike NISD, NERC-CIP allows penalties to be levied for non-compliance with the regulations, regardless of whether an incident has occurred, which has led to criticism that the industry needs to spend significant money on compliance (and evidencing that compliance) – money which would be better spent on improving security.
The concept of resilience is not new, of course, and to a certain extent, building robust digital systems is just another element of resilience. However, one aspect that companies could better manage and control is protection from malicious attack.
“There have been some spectacular examples of cyber attacks recently,” Buffey says. “Those against a Ukrainian power system are probably the most high-profile.” While it has been widely assumed that Russia was behind the attack, there is no publicly available evidence that this is the case.

Technical Director, Aerospace,Defence, Security & Technology
“That is one feature of cyber attacks – attribution is very difficult. There are justified fears about cyber warfare and attacks on critical infrastructure. The fact is that we are likely to see more like the Ukraine attacks, which are almost like an alternative to economic sanctions,” he adds.
Before the Ukraine attacks, there was a widespread assumption that not only were such attacks not possible, but also that no one would want to perpetrate them.
The WannaCry attack earlier this year, which caused severe disruption to the UK’s National Health Service, Germany’s rail network, FedEx and a host of others, attacking more than 300,000 computers in 150 countries, highlighted the number of organisations with computers that run out-of-date software or fail to fix vulnerabilities in their systems. It is not just hospitals that are vulnerable – a lot of critical infrastructure has old computer systems, because they were built to last at a time when today’s digital connectivity had not been considered. The same goes for military installations and equipment, much of which has been in service for decades.
The key to making national and private infrastructure and networks more secure is to take security concerns into account right from the start.
If security resilience is designed in from the beginning, it is much cheaper and easier – retrofitting is always more expensive and problematic.
“To a certain extent, the technology can be the easy part. We know most of the things that we need to do and putting the right measures in place can make a big difference,” Buffey says. “But maintaining it afterwards can be difficult, because cyber awareness is still not always embedded in business culture. There is a real need to change perceptions so that organisations treat it with the importance that it deserves.”
In this regard, your workforce is both your greatest asset and your biggest risk. They can highlight when something has gone wrong, but they can also introduce vulnerabilities.
While many products on the market claim to help to improve cyber security, technology on its own is not enough. “We prefer to have a long-term relationship with a client, because quick fixes don’t really achieve anything,” says Buffey.
However, for companies offering advice in this area, it can be hard to make the case for action. Buffey says, “You are telling people: ‘this is something that you’ve never had to worry about before, but now you do and you’ll never be finished.’ It is not an attractive sell.
Find out more about cyber resilience
VISIT OUR CYBER HUB“The fact is, though, that the idea that you will completely prevent attacks has gone. Everyone accepts that. You have to plan for the day when you do get attacked.”
One looming danger is the growing complexity of the digital landscape. With some artificial intelligence programmes acting in ways that their creators do not fully understand, and the increasing integration between parts of the economy that have previously been unconnected at the network level, the risks abound.
“It used to be that even for a complex project, one person would be able to understand the potential cyber risk,” Buffey says. “Now, when everything is all linked together, no one person can grasp the whole thing. The integration of different systems and the relationship between them is something that most organisations have not yet got their heads around.”
“Big infrastructure projects and services are vulnerable to attack due their size and complexity, and because their systems are so widely distributed, with multiple connections resulting in a host of potential access points,” Glazebrook says. To totally secure them would be very costly and is often unrealistic. Understanding that an attack will happen therefore means we also need to ensure systems and services are resilient to the impact of an intrusion.
“It is in this area that we are likely to see most innovation,” says Fielding-Smith. “A lot of innovation will come in the process of integrating new technology. The smart stuff will be in how we bring it all together.”
The need for resilience is where the digital revolution is most obviously limited. “The best way to protect a system is to not connect it to the network,” Fielding-Smith adds, but this is no longer viable. “Failing that, critical infrastructure needs to be simple, so it can be tested to see if it performs as required under all conditions.”
One useful tool is simulation, as Atkins has discovered in its work on implementing the European Railway Traffic Management System in Denmark. “We found that as you integrate the railway, drawing upon elements from multiple suppliers, it is essential to have a simulation lab where you can put it all together,” says Fielding-Smith. “It can be used to prove cyber security, and if you have a simulation set up as a reference, as you upgrade software you can continue to test for security and probe vulnerabilities offline.”
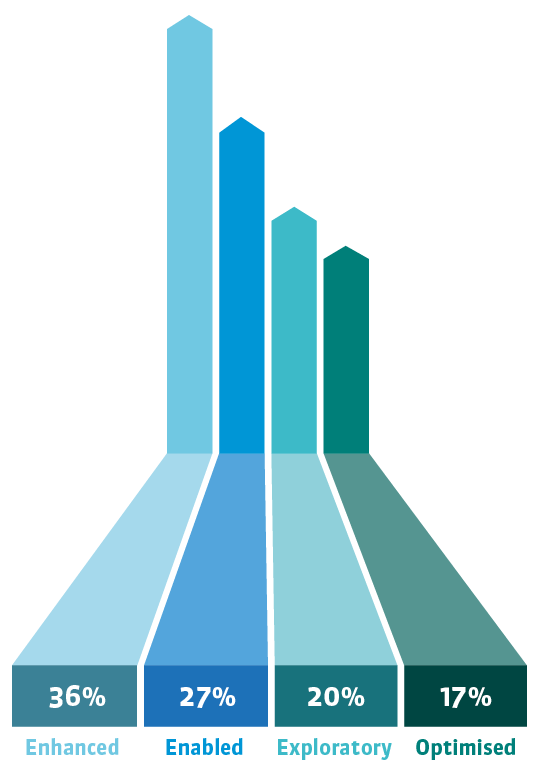
Where does your company sit on the digital transformation maturity spectrum?